Russian Drones in Ukraine Hacked: 'Russian Hackers to the Front' group and frontline operators suffer drone network compromise at the hands of unknown cyber actor.
Recently, a cyberattack disrupted the infrastructure and network used by Russian volunteer group 'Russian Hackers - to the Front' (RHF) and frontline Russian operators.
RHF are a volunteer group, who develop and distribute specialized Russian drone firmware known as '1001', which enables the conversion of consumer-ready drones for military operations in Ukraine. Pro-Russian UAV support channels suggest that RHF was set up by US-sanctioned cyber security company, Positive Technologies. The company had previously been sanctioned for developing weaponized exploits for the Russian Government and intelligence services, facilitating their cyber campaigns.
Disclosed via their pro-Russian Telegram channel, RHF stated the breach involved unauthorized access to servers responsible for pushing firmware updates to drone operator stations. Attackers reportedly deployed messages to users’ screens before disabling their systems, causing significant operational disruption. The network supports a closed-loop deployment model in which pre-configured laptops, referred to as 'terminals' distribute updates to drones via secure service centers.
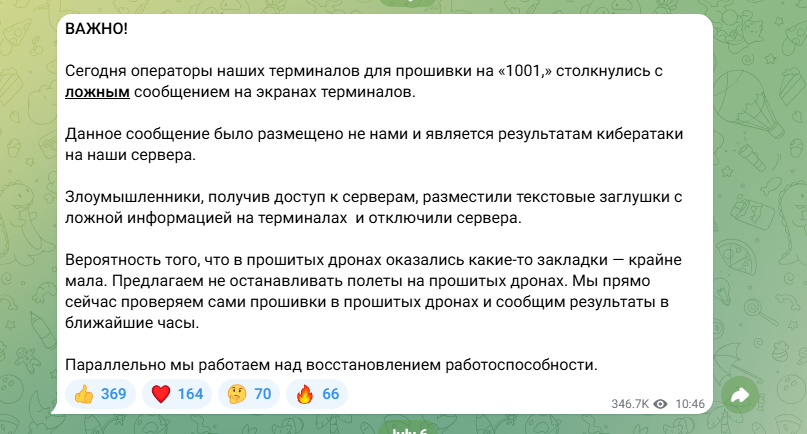
According to independent Russian cybersecurity analyst Oleg Shakirov, the attack likely targeted the central remote server used to control firmware distribution. 'No actor has claimed responsibility yet', Shakirov noted, 'but the operation demonstrated a high level of technical expertise and knowledge of the firmware’s delivery architecture'.
Many drone brands continue to be extensively used in combat roles. DJI drones see widespread use, despite the Chinese manufacturer’s opposition to military use and its alleged decision to halt direct sales to Russia. Multiple drone models are procured through third-party resellers and modified to bypass embedded restrictions. The 1001 firmware is not publicly available and is distributed exclusively through RHF service centers. It is used to reprogram the DJI drones, lifting manufacturer-imposed flight restrictions, improving resilience against GPS spoofing and enabling the use of high-capacity batteries and other upgrades. The firmware change also lifts restriction on height, distance and payload limits on the drones, making these commercial platforms viable for frontline use. As of September 2025, developers stated that roughly 300,000 drones had received the update.
Despite RHF’s claim that the firmware was not compromised, the incident highlights the vulnerabilities in Russia’s tactical tech infrastructure. RHF administrators have not confirmed just how widespread the damage actually is, and with Russian drone units being a high priority for Ukraine, operators were advised to disconnect terminals as a precaution. This move could restrict the Russian military’s ability to update or deploy modified drones on the battlefield, and will almost certainly cause distrust amongst operators regarding the technical capability and reliability of their equipment.
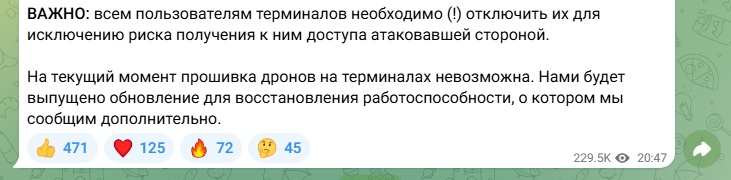
This marks one of very few instances where a Russian military-adjacent developer has publicly acknowledged a cyber intrusion. It echoes broader trends in the conflict, where other Russian systems (particularly those tied to real-time battlefield intelligence and drone integration) have been targeted in cyber operations.
This latest attack highlights the inherent risks in digitally tethered battlefield systems, and how Russia's increasing reliance on civilian and third party support makes them vulnerable to adversaries on the contemporary battlefield. As RHF administrators have not confirmed the extent of the network disruption, the scale of the threat remains to be seen, potentially putting operators at serious risk if equipment continues to be used.